The first article in a series to help you understand the use of the Kraken Stress Testing Toolkit.
This test is not a full-fledged load testing but only demonstrates an example of server diagnostics and Kraken capabilities.
Test environment
The test web server is deployed in a virtual environment based on Centos 8 Stream.
Number of processor cores: 3
RAM capacity: 2 GB
Hard disk capacity: 60 gigabytes.
The following components are deployed on the server:
The web application chosen for testing was bWAPP
Buggy web application (bWAPP) is an open source web application. It is designed to find and exploit vulnerabilities in web applications.
The web server is accessible by the domain name test.local
Changes made to the server configuration
- Disabled SElinux
- Apach is configured in prefork
- Apache access log buffering is configured
Choosing a template for testing
The “HTTP Rand Param” was chosen as the template for testing, emulating the A recently discovered DDOS attack from WordPress sites.
Also, this template randomizes the user-agent, from the variable %user_agent%
This template is a standardized template:
[MAIN]
name=HTTP Rand Param
index=?%rn_str%
UserAgent=%user_agent%Monitoring setup
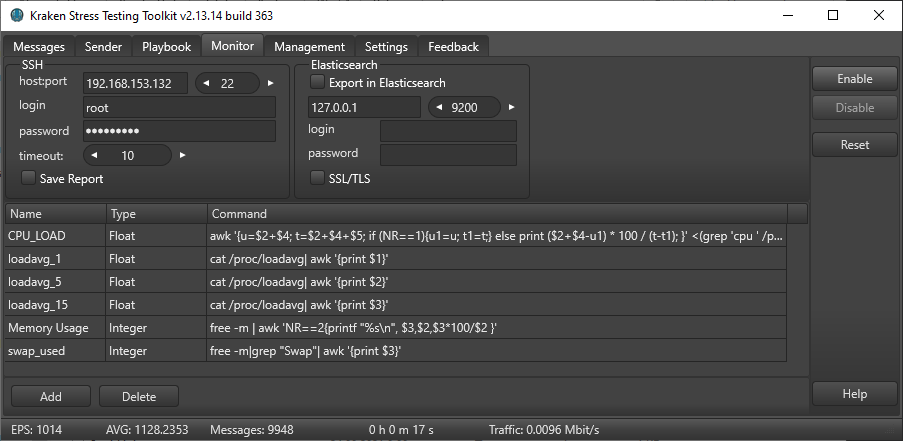
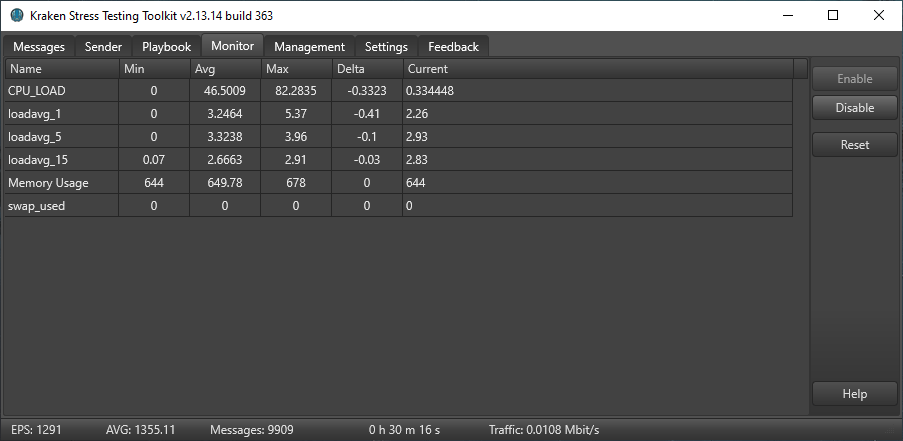
The following were selected as monitoring criteria:
- Current CPU utilization
- Load Average for 1 minute
- Load Average in 5 minutes
- Load Average in 15 minutes
- RAM utilization
- Disposing of the swap file
The appropriate data types (Integer and Float) are configured.
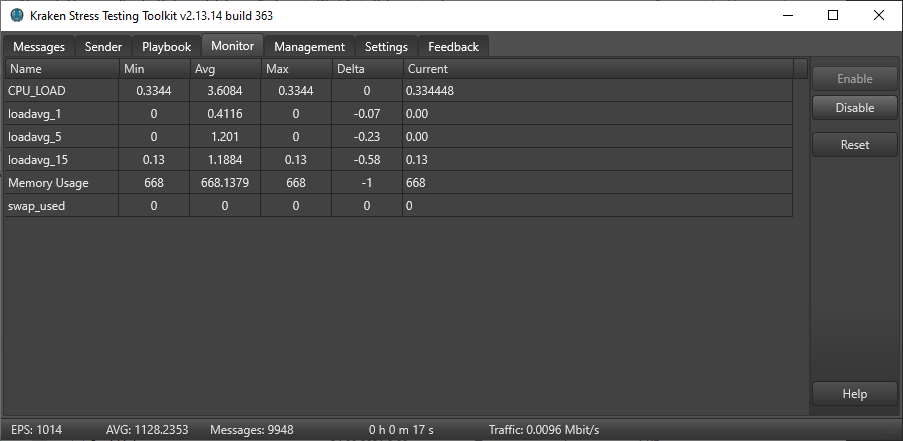
Example of unloaded data:
Configuring the sending of events
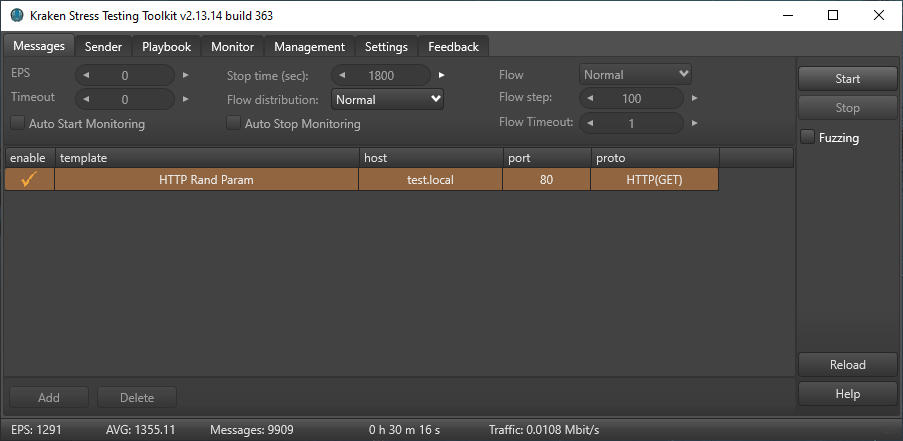
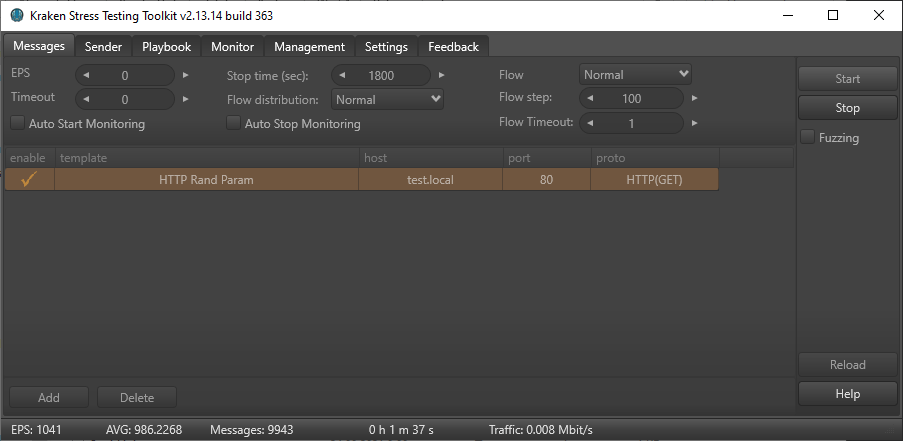
Configuring the sending of kraken events is done on the Messages tab.
Add a new line by pressing the “Add” button, and then in the drop-down list select the necessary template
In the same way choose the sending protocol, for the test we will choose asynchronous method of sending HTTP Get requests.
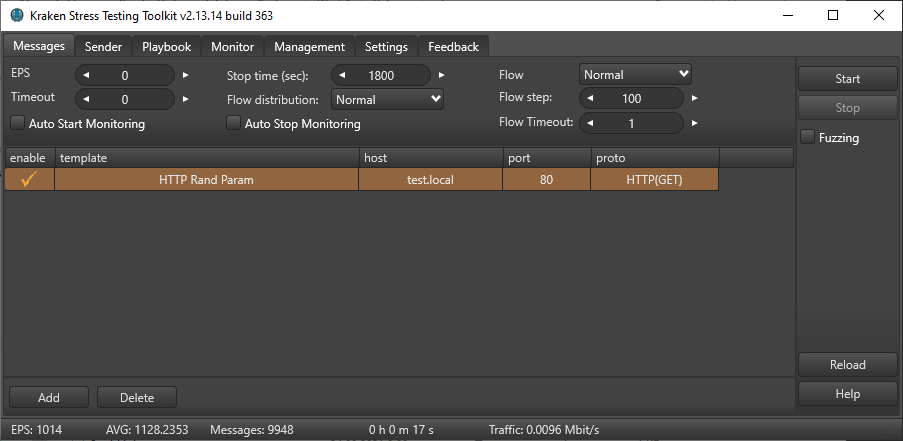
Specify the connection host and port in the corresponding fields
The test time (Stop time) is 1800 (30 minutes).
EPS is set to 0, so that Kraken sends events without restrictions, as it is necessary to determine the maximum load possible on the web server.
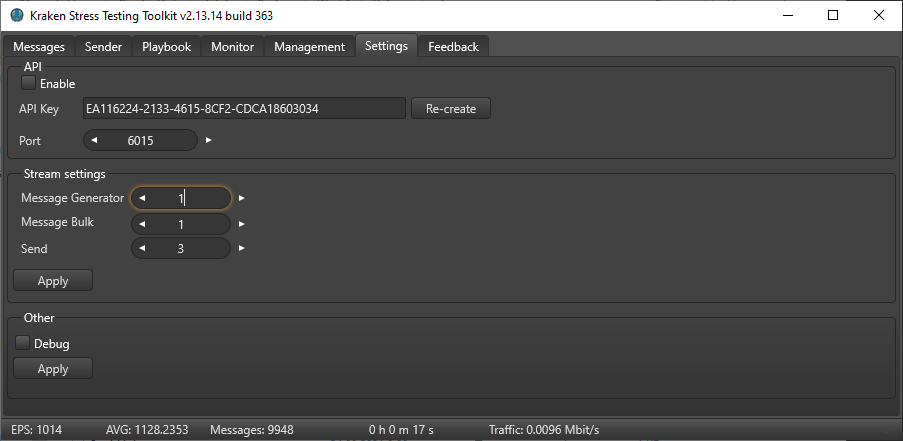
Additional kraken settings
Additionally, we'll change event generation and sending parameters.
Number of event generators: 1
Beam size, in generator: 1
Number of sending streams: 3
First test results
After the start of testing, the system experienced a significant load on the system by the daemon tuned.
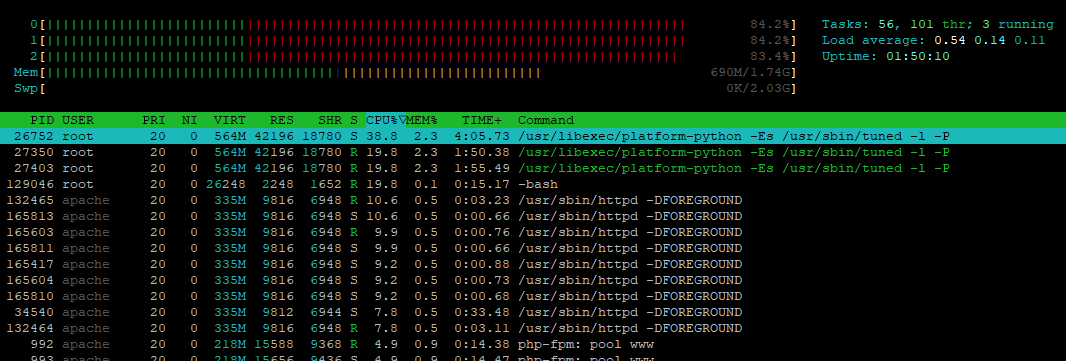
This sends about 950 events per second to the server
the demon has been shut down to reduce the load
service tuned stop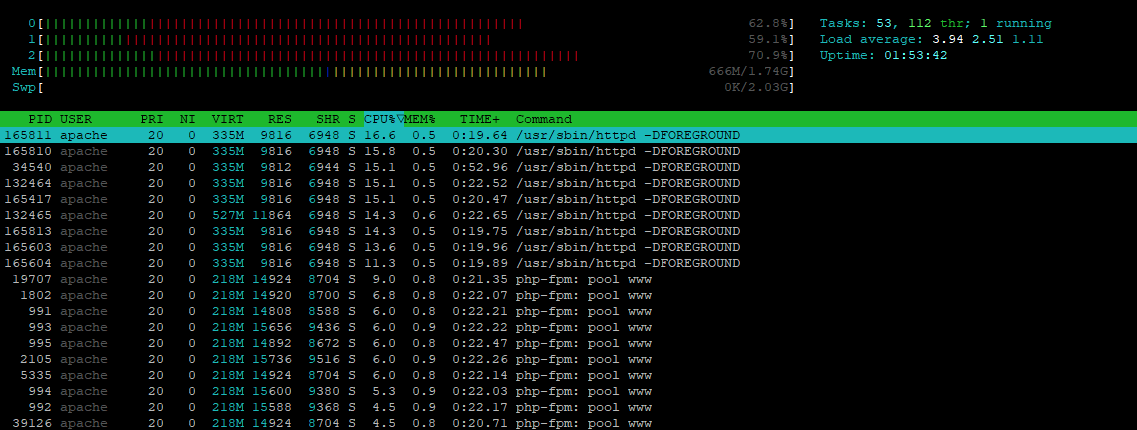
The result was an increase in the number of events sent per second, over 1000 RPS
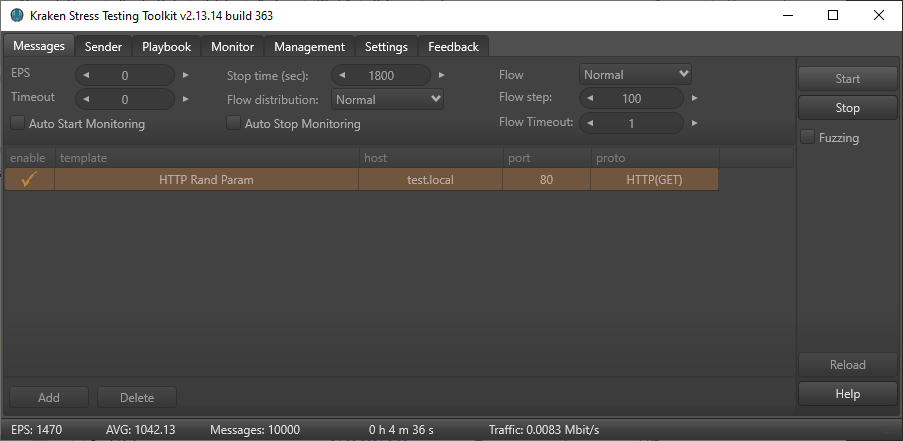
Test results
At the end of testing, the average event stream was about 1300 RPS. The average CPU utilization was 38%, the maximum Load Average was 5.3 while the daemon was tuned.
Summary conclusions
- Apache + PHP can handle a significant number of requests
- The bottleneck may be MySQL, since bWAPP only uses it on some pages, MySQL had no impact on system performance.
- tuned can create additional load in an attempt to optimize.